Menu
How our Cloud email security works

Robust and intelligent multi-layered email security
Cyberattacks are more and more clever. Multiple sources of email threat protection are necessary to better protect email ecosystems nowadays.
Our global infrastructure and the real time intelligence we can correlate from and to our systems worldwide, ensures our filtering performance is very effective and, especially, efficient detecting threats as they start.
- Deep Content Inspection for fully capable filtering of content
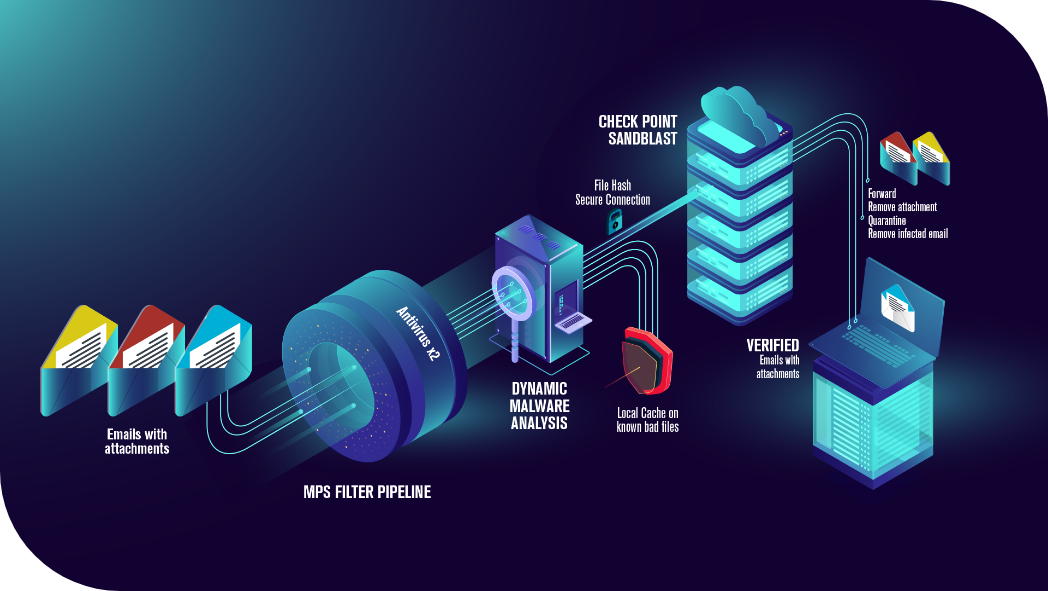
- Use of 3 well-known antivirus engines: Sophos, Bitdefender and ClamAV
- Integration with other antiviruses for zero hour burst detection
- Own machine learning heuristic analysis
- Attachments search and blocking by filetype
- Propagated Blacklists and Whitelists
- Real-time reputation analysis
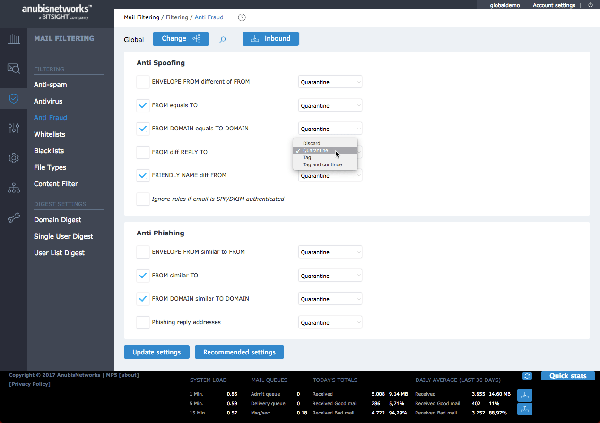
- Anti-fraud engine (for phishing and spoofing)
- Data leakage protection
- Spam waves protection
- TLS and DKIM Encryption
- Authentication verification (SASL, DMARC, …)
- User Credential Theft protection
- Optional: malware sandbox with CheckPoint

Bitsight’s data sharing
200 different malware families tracked permanently, some potentially involved in spambot campaigns.
10 million spam processed per day on our honeypots and an equivalent number in our live systems.
Constantly updated reputation on 30 million active IPs, with a database of around 40 million bad reputation IPs.
Shares daily threat information from existing Telcos, corporate and SMBs existing clients.
Real-time threat intelligence
Our service ensures your system is always up-to-date with the latest threats detected in our ecosystem, obtaining:
- Email fingerprinting close and exact match with a global database of spam, phishing, and malware email
- Reputation on the sender, and sudden reputation changes
- Reputation requests, and flow counts, which may indicate spam waves and active spambots
- Known infections by botnet families, especially with malware knows to use email attack vectors
- Social references in Dark social web to lost credentials
- Evaluation of DKIM and SPF for spoofed accounts

Email control
Control of the extruded data, of the email flow, and of the user integrity are just as important.
- Data Leakage Inspection for Outbound Emails
- Quota management per Scope
- HTML digests for release, tag and fast whitelisting
- Virtual Aliases and Email routing per user
- UI on https and with Authentication policies
- Privacy features for preventing Top levels from seeing emails down the hierarchy without explicit authorization
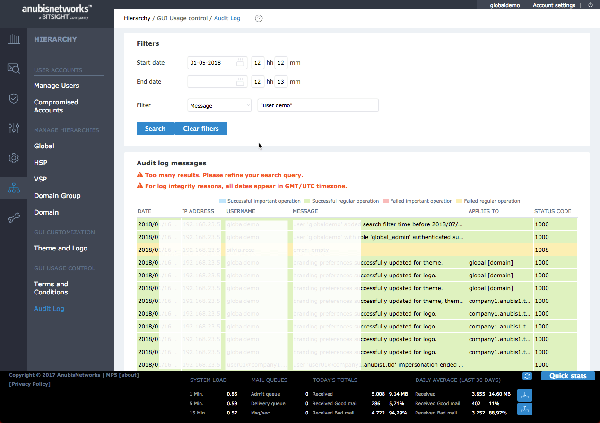
- Full system Auditing
- Email Disclaimers
- Helpdesk accounts with restrictions over special email accounts



Full integration with every Email Server
Includes cloud converged solutions Microsoft Office 365 and G Suite.
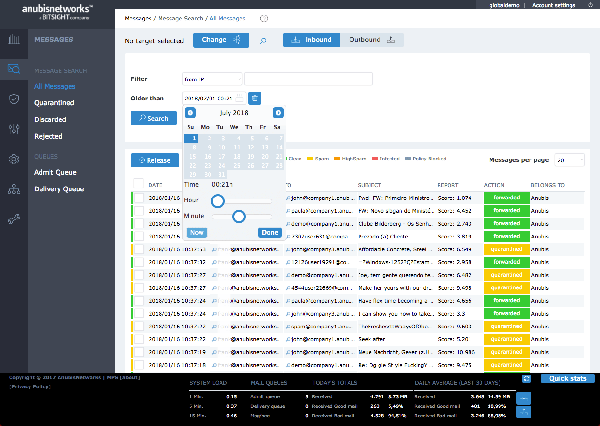
Email security in action

Thorough verification of emails
A point system analyses senders’ reputation, emails attachments, email signatures, URLs within emails

Flexible configuration and quarantine
Quarantine can be managed by IT and/or end users, in a centralized console, with the option of web end user interface and/or email interface (via periodic digests):
- Personalized email digest for Quarantine release and/or UI access to end users, as frequent as one per hour
- Daily report to users of emails in quarantine
- The IT admin can:
- Virtual Aliases and Email routing per user
- UI on https and with Authentication policies
Configure the service yourself, or ask one of our technicians to do it for you.

Multitenancy
Unique Multitenant system for facilitating the security and operationalization of the platform.
- A unique system, which allows multiple levels of hierarchy for delegated administration, with settings propagation, inheritance and auditing over changes.
- Several types of administration, support and operations accounts.
- This virtual hierarchy is “tailor made” for Telcos, Service Providers and resellers, which can use the same cloud environment (personalised) for containing their own branch of shared end organizations.

Verify email fingerprints, domain reputation and new malware strains
- Email fingerprinting close and exact matches with a global database of spam, phishing, and malware email.
- Reputation on the sender IP, and sudden reputation changes and reputation requests count, which may indicate spam waves.
- Known infections by botnet families, especially with malware knows to use email attack vectors.


Analytics
Be master of your next action:
- Live Dashboard for Inbound and Outbound data on classification, filter actions and other KPIs
- Queue management, throughput, and rejections scope
- Historic statistics
- System Scheduled Reports
- Hardware and Software monitoring
- Services monitoring
- Rejected messages tracking
- Integration with 3rd party systems via Syslog
- Training the system
- Deep information on each message. With visibility to all scopes and end-users.
- Business related information and complete system auditing

Resiliency
Integrates seamlessly with your security patterns and networks infrastructure
- Using Web services makes it extremely easy to with existing email platforms, webmail and portals.
- The architecture, originally built for Cloud scalability, possess some of the most advanced techniques for ensuring deployment in complex environments. This includes No-SQL database full replication, integration with Load Balancers, and integration with other business modules, such as DLP and archiving.
- Integrated and seamless user experience; no need to go to different applications to manage the email security settings.
- Can be integrated with Telco’s IT infrastructure (e.g. Billing, Order Management, Middleware and Provisioning systems) for complete process optimization.

 English
English Deutsch
Deutsch