Menu
Compromised Accounts
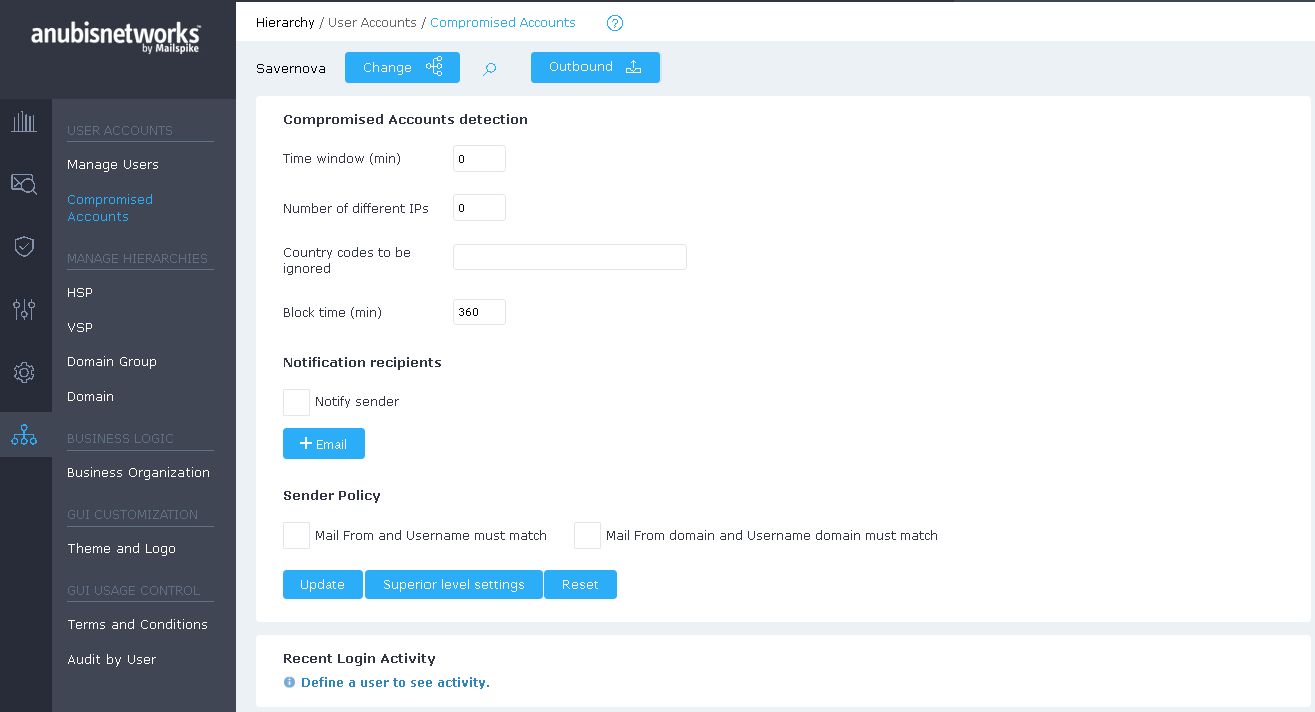
Compromised Accounts Detection
This section allows you to identify possible compromised accounts by analysing the frequency and origin of access logins.
The notion behind an account being compromised is related to the impossibility of a human to send messages from very different locations, in a short amount of time.
To configure compromised accounts, you must select a Hierarchy scope, a Domain scope, or a single User (email address), and then:
- Set the Time window, in minutes, to count the number of different logins.
- Set the Number of different IPs that should be allowed during the Time window previously set.
- Set the Country codes to be ignored to exclude countries for which to check IPs geolocation. Several countries can be added by adding TLD level codes, separated by commas. (E.g., RU, US).
- Set the Block time, the number of minutes the user's ability to log in is blocked by the system (access denied).
You can also decide on email addresses to receive a notification once the limit has been reached, by adding complete email addresses to the Send email to box/boxes:
Several email addresses may be included, by clicking on the "+Email" button.
Email addresses may be excluded by clicking on the "Delete" (Garbage Can sign) button.
The Sender can receive notifications, by checking the "Notify sender" box.
Sender Policy
These restrictions will apply permanently:
Tick "Mail From and Username must match" to ensure the email address is the same as the username used in the login.
Tick "Mail From domain and Username domain must match" to ensure the email is the same as the username domain used in the login
Click "Update" to activate the changes above.
Click "Superior Level Settings" to have settings inherited from the Hierarchy Scope above.
Click "Reset" to set the settings to null and disable the feature.
Recent Login Activity
MPS can list, per user, the successful login details in terms of Time Window, Number of Different IPs, and status (if blocked). Logins from ignored countries and Sender Policy restrictions will not be listed.
On each table, you will be able to see:
Status: If it is blocked, and until what time.
(Table column) Last login GMT: the time of the user's last login, from a given IP address; times are normalized to GMT timezone.
(Table column) IP Address: The corresponding IP address for the last login.
(Table column) Country: The country name and flag attributed to the IP in the previous column.
(Table column) City: The city attributed to the IP in the previous column.
By clicking on Reset activity, all records will be deleted, and the set counters (e.g. Time window and Number of different IPs) will restart from that user, starting from the clicking moment.
 English
English Deutsch
Deutsch